Around 92% of money in the world is digital, so it is no surprise that online transactions are increasing consistently. But are the security standards that usually accompany traditional bank transactions met by online transactions?
According to Statista, e-commerce sales have increased from 1.34 trillion US dollars in 2014 to 2.84 trillion US dollars in 2018, i.e. the value of online transactions has more than doubled worldwide over four years. These rapidly increasing sales figures are indicative of a growing reliance on online shopping for things from plane tickets to groceries. And why wouldn’t you order everything from the comfort of your sofa if you could?
The problems begin when we explore the security of online payment services, and how much online vendors deserve our trust when we provide them with credit card details and thus access to our hard-earned cash.
Although traditional bank robbery is largely relegated to the cinema, banks are still not immune to money being stolen from their reserves. In 2015, a global attack on more than 100 financial institutions extracted £650 million.
Many institutions internationally have glaring cybersecurity gaps, which need to be addressed if we are to continue to trust banks with our hard-earned money. However, banks aren’t the only guilty party when it comes to neglecting cybersecurity.
Even in countries like the USA, the home of Silicon Valley and hundreds of hi-tech multi-nationals, the government is struggling to keep up with emerging cybersecurity threats. The cities of Atlanta, Riviera Beach, Lake City, and Baltimore have all conceded to ransomware attacks because of lacking cybersecurity practices and training. Preventable attacks such as e-mails with malicious .xls files or phishing should not be as substantial a cause for attacks nowadays.
The best protection is, of course, prevention.
All your software should be updated to the latest version to ensure known vulnerabilities are patched and utilise antivirus software which will detect malware before it can be executed and do any harm.
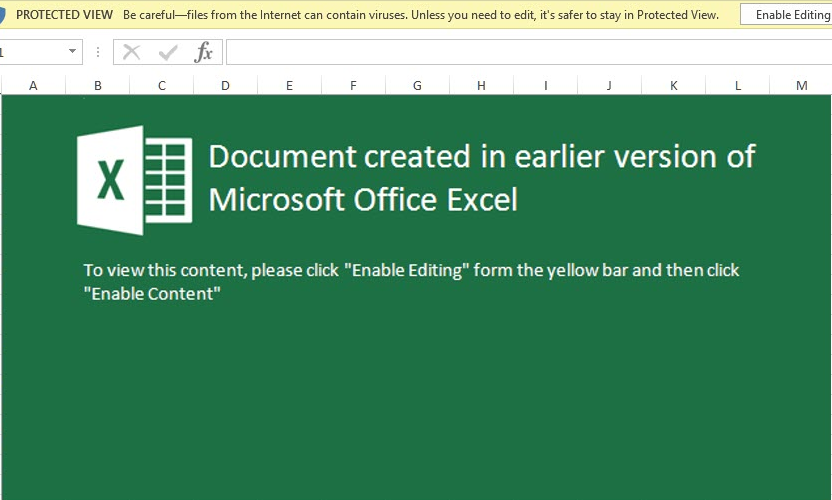
If an e-mail is from an unverified or untrusted source, as a rule, don’t download any attachments. While most people who are somewhat tech-savvy would be naturally suspicious of an .exe file attachment, a Microsoft Office file may not flag the same suspicion.
Through utilising macros, however, attackers can implement malicious VBA code, which then can be used to run PowerShell code to download and execute malware. If you don’t typically have macros enabled in Excel, do not enable it for any excel documents that came over e-mail, unless you are sure it is a trusted source.
As the world grows to be more interconnected, we share more data than ever on our machines through cookies, online transactions, or simply browsing the web. That data, when stored and used by banks, resellers or otherwise, becomes increasingly critical.
It’s even relatively understandable why people succumb to the demands of ransomware attackers. However if you have multiple access points – i.e. numerous data backups – and one of those access points is hit by ransomware, it’s an inconvenience but nothing beyond that.
Of course, having strict backup routines and having separate places to store the data is an expensive and challenging procedure, but when you look at the amount of money you’d have to pay attackers to get your data back otherwise, it pays off to be safe.
Do you trust your money is safe? Does the security of banks and financial institutions concern you? Let us know on Twitter or LinkedIn (or both).