Proactive cyber defense for your business
Minimise risks with next-gen prevention
Multilayered,
prevention-first
Cutting-edge AI meets human expertise
World-renowned threat intelligence
Hyperlocal, personalised support
Multilayered,
prevention-first
Cutting-edge AI meets human expertise
World-renowned threat intelligence
Hyperlocal, personalised support
"ESET products are on top of their game.
Excellent value and performance."
IT manager, education industry (via Gartner Peer Insights)
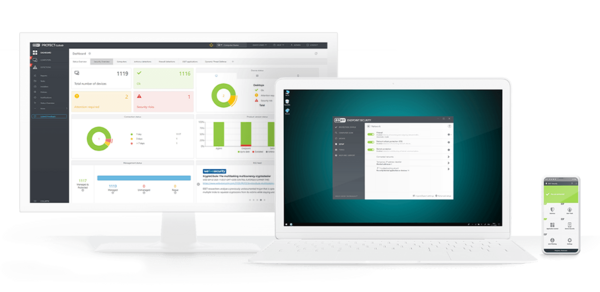


We are a leading digital security provider with prevention-first technology, able to identify and neutralise different threat attack vectors before they can be exploited, providing best-in-class protection against the most advanced cybercriminals.
Read case studies
Useful links
Learn more about:
We highly recommend you install and deploy our solutions through ESET’s management platforms (cloud or on-premise, depending on your preference). Managing your endpoints centrally saves time, is more efficient and provides 24/7 peace of mind. Use of our security management console is included free with your licence. Setting up ESET solutions is quick and easy, and we will guide you through the process. Start now.
If you’d prefer to download our software locally, you can download with installers here.
If anything is unclear, please check our detailed step-by-step guides or contact our team.
If you have ESET home product installed, and wish to switch to a different ESET solution, please uninstall following these instructions. Once this is completed, please attempt to install your newly-chosen ESET product again.
If you already have an older business version installed, upgrade to your security into the most recent version using this guide.
ESET has recently simplified its offering, so it there may appear to be several products ‘missing’ which you’ve previously seen on our website. Please don’t worry; we still offer all the great products that we did before, just grouped more simply under adjusted product names.
A deciding factor for cloud solutions is how ‘savvy’ your company is with managed or unmanaged software. Considerations such as whether you have in-house IT or employ ad-hoc IT support should also influence your decision.
ESET PROTECT Cloud (formerly ESET Cloud Administrator) is a cloud-based management console (offered as a service) which enables centralised management of select ESET products. ESET PROTECT Cloud enables you to manage your company's network security without the need to buy, install or maintain additional hardware.
Our sales team would be more than happy to discuss your company’s requirements and recommend the best ESET solution for your needs; contact them today.
ESET Business bundles offer multiple ESET products under a single licence. This unique licencing system allows you to protect all of your company’s computers, laptops and smartphones using ESET solutions, without purchasing individual licences for each operating system
Absolutely. If you want to see our ESET PROTECT management platform in action, try our interactive demo. No installation is needed and you can experience first-hand how your cloud management will look after few weeks of use.
If you are more interested in testing the full-feature licence, please request a free trial. You can install and deploy our protection solutions and test them free for 30 days, without any commitment. If you are interested, our experienced UK-based team will contact you and discuss any additional questions or specific business requirements you might have.
The cost of your digital security is not just the visible cost of a licence, but also the cost of managing it. ESET has a light footprint on your system, ensuring that there is little or no effect on your productivity or even your energy consumption; we call this The ESET Advantage. Find out how much ESET could save you annually.
Verified customers appreciate that ESET has:
“Sleek interface and works as expected every time. All policies and remote administration is straightforward and thoroughly documented if there are questions.”
Read the full review and more on ESET’s G2 profile.
We are committed to our clients’ satisfaction and therefore offer a generous 30-day return policy. If you are not 100% satisfied with your purchase, we will be happy to provide a full refund of the purchase price.
You can renew, enlarge or upgrade your licence at any time. This keeps your product up to date, maintains your uninterrupted protection, and ensures you have free access to our technical support as well as loyalty benefits.
If these options are not present in your account, it’s likely that your licence has already expired. If this is the case, we recommend purchasing a new licence.
ESET auto-renew ensures that your ESET licences and products are always up to date, providing continuous, year-round protection. We handle the billing and renewal for you using auto-renew, and you’ll be entitled to special renewal pricing.
By enabling auto-renew, you agree that at the end of your licence period, we will automatically renew your licence using the payment details currently on file. For more details, see our auto-renewal policy.
We will inform you about upcoming auto-renewal and renewal prices 30 days before your renewal date (for annual subscriptions) and after your subscription automatically renews, we will email you the transaction details.
Auto-renew is continuous, unless you turn it off after your purchase, via your account. Turning off auto-renew will not cancel your licence – your ESET protection will continue until your licence expires. We will notify you before licence expiration so you may renew manually.
You cancel automatic renewal at any time.
Brought to you by awarded and recognised security researchers from ESET's 13 global R&D centres.
Please select the licencing option most relevant to your business, depending on the number of seats you would like to protect.
INSTANT TRIAL
Fewer than 20 seats
More than 20 seats