How this solution will help you combat cyber risks
Advanced protection for Microsoft 365 & Google Workspace apps
Protect your cloud email, collaboration & storage
Our combination of anti-malware scanning, spam filtering, anti-phishing and proactive threat defense helps protect your organization against infections and targeted attacks, as well as blocking new, never-before-seen types of threats, especially ransomware.
One-click data encryption
Protect business data
Helps comply with data regulations thanks to full disk encryption capabilities on Windows and macOS.
Advanced multilayered technology
Secure computers, mobiles, file servers
Company endpoints and mobiles are protected via advanced multilayered technology, including file server security, now with brute force attack protection.
Set up and deploy within minutes
Enjoy easy-to-use management
Single-pane-of-glass remote management for visibility to threats, users and quarantined items.
Vulnerability and patch management
Automatically track and patch vulnerabilities
Reduce cyber risks to the lowest level. Get easy-to-use, effective support for assessing third-party software vulnerabilities with fully automated patch management, all from a single pane of glass.
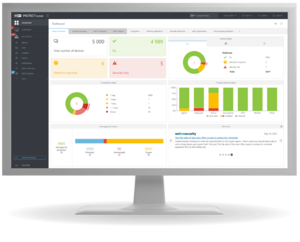
Management Console Unified cybersecurity platform interface providing superior network visibility and control. Available as cloud or on-prem deployment.
Learn more
Modern Endpoint Protection Advanced multilayered protection for computers and smartphones powered by unique ESET LiveSense technology.
Learn more
Server Security Real-time protection for your company’s data passing through all general servers.
Learn more
Mobile Threat Defence Robust security for all Android and iOS mobile devices within the organisation. Equip your mobile fleet with Antimalware, Anti-Theft and MDM capabilities.
Learn more
Full Disk
Encryption Robust encryption solution for system disks, partitions or entire devices to achieve legal compliance.
Learn more
Advanced Threat
Defence Proactive cloud-based prevention against ransomware or never-before-seen threat types with autonomous remediation capabilities.
Learn more
Cloud App Protection Advanced protection for Microsoft 365 and Google Workspace apps, with additional proactive threat defence.
Learn more
Mail Server Security An additional layer of security, protecting Exchange and IBM email servers from threats entering the network on top of the standard endpoint and file server protection.
Features advanced anti-phishing, anti-malware, and anti-spam combined with cloud-powered proactive threat defence. Provides you with robust quarantine management and rule definition/filtering system.
Prevents ransomware and other email-borne attacks without compromising email's speed.
Learn more
Vulnerability & Patch Management Actively track & fix vulnerabilities in operating systems and applications across all endpoints.
Learn more
This module is available in ESET PROTECT MDR.
Extended Detection & Response
This module is available in ESET PROTECT MDR.
Multi-Factor Authentication
This module is available in ESET PROTECT MDR.
This module is available in ESET PROTECT MDR.
Premium Support Essential
Full visibility of your network and endpoints, wherever you are
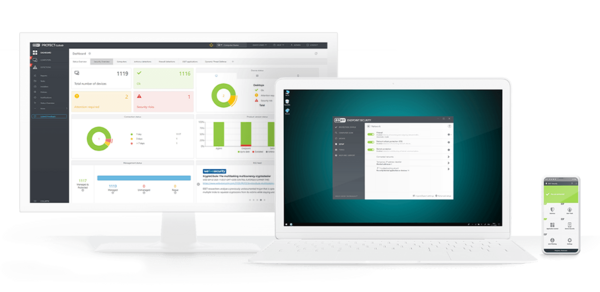
Experience the console's full potential right now.
No need to install or set up anything.
Advanced reports
ESET PROTECT platform provides over 170 built-in reports and allows you to create custom reports from over 1000 data points.
Custom notifications
Use predefined notifications or create your own. The notification system features a full “what you see is what you get” editor.
Single-click management
Actions such as create an exclusion, submit files for further analysis or initiate a scan are available within a single click.
What IT pros are saying

Angela S
"It is very much customisable tool. In my opinion it is the most functional, robust and manageable tool than any other."
Read full review

Jason D
"The interface is easy to use and lightweight on the system. When used on a 4+ core device with an SSD, the system impact is negligible for most office tasks."
Read full review

Jaliya S
"It is easy to use, simple and understandable. Therefore, we can easily manage the features of it. Also, it is easy to install, configure and update. "
Read full review

Jen D
"I love the way it helps us in detecting unnecessary things that are continuously running our systems behind. In this way it enhances the security of our system."
Read full review
Based on customer reviews, through G2 Crowd surveys that asked ESET business customers to rate their experiences using ESET PROTECT solutions.
Get started

protected by ESET since 2017
more than 9,000 endpoints

protected by ESET since 2016
more than 4,000 mailboxes

protected by ESET since 2016
more than 14,000 endpoints
ISP security partner since 2008
2 million customer base
System requirements and subscription information
ESET PROTECT Complete
Supported operating systems
For computers
- Microsoft Windows 11, 10, 8.1, 8, 7, SP1
- macOS 10.12 and later Ubuntu Desktop 20.04 LTS and 18.04 LTS 64-bit
- Red Hat Enterprise Linux 7, 8 64-bit with supported desktop environment installed
- SUSE Linux Enterprise Desktop 15 64-bit
For smartphones and tablets
- Android 5 (Lollipop) and later
- iOS 9 and later
For file servers
- Microsoft Windows Server 2022, 2019, 2016, 2012, 2008, R2 SP1
- Microsoft Windows Storage Server 2012, 2008R2
- Microsoft Windows Small Business Server 2011
- RedHat Enterprise Linux (RHEL) 7, 8
- CentOS 7, 8
- Ubuntu Server 16.04 LTS, 18.04 LTS, 20.04 LTS
- Debian 9, 10, 11
- SUSE Linux Enterprise Server (SLES) 12, 15
- Oracle Linux 8
- Amazon Linux 2
For mail servers
- Microsoft Exchange Server 2019, 2016, 2013, 2010, 2007
- Microsoft Windows Server 2019, 2016, 2012, 2008
- Microsoft Small Business Server 2011
- IBM Domino 6.5.4 and newer
- HCL Domino version 11, 12
For cloud applications protection
- Subscription for Microsoft 365 or Google Workspace to connect with the tenant (Exchange Online, OneDrive, SharePoint Online, Teams, Gmail, Google Drive)
Licence information
Cloud and on-premises management included
Remote management platform is available as cloud-based or on-premises deployment. No need to buy or maintain additional hardware, reducing the total cost of ownership.
Flexible licencing
Mix and match your licences as needed
ESET Unilicense covers all the bases, allowing you to mix and match endpoint protection without wasting a single licence.
Add additional devices at any time
You can purchase licences for additional computers, laptops, mobile devices and servers any time.
Transfer a licence to another computer
You can transfer a valid ESET licence to a completely new computer from the original one. In addition, you can switch from one OS to another.
Switch to a different platform at any time
It's easy to switch your protection from one platform to another at any point during the licence term without having to purchase additional licences.
Frequently Asked Questions
How do I download/install the solution after?
We highly recommend you install and deploy our solutions through ESET’s management platforms (cloud or on-premise, depending on your preference). Managing your endpoints centrally saves time, is more efficient and provides 24/7 peace of mind. Use of our security management console is included free with your licence. Setting up ESET solutions is quick and easy, and we will guide you through the process. Start now.
If you’d prefer to download our software locally, you can download with installers here.
If anything is unclear, please check our detailed step-by-step guides or contact our team.
I already have another ESET product or version installed, what do I do?
If you have ESET home product installed, and wish to switch to a different ESET solution, please uninstall following these instructions. Once this is completed, please attempt to install your newly-chosen ESET product again.
If you already have an older business version installed, upgrade to your security into the most recent version using this guide.
I am unable to find a specific endpoint security product that was once offered
ESET has recently simplified its offering, so it there may appear to be several products ‘missing’ which you’ve previously seen on our website. Please don’t worry; we still offer all the great products that we did before, just grouped more simply under adjusted product names.
- We have added new security solutions to our offering (e.g. cloud sandboxing technology or cloud apps protection) and renamed old bundles. You can find out more about the changes here.
- Some products are currently only available only through speaking to a member of the ESET sales team. For example, this is true for our entry-level security ESET Endpoint Antivirus and bundles based on it, as well as certain on-premises variants of higher-tier bundles. If you are interested to purchasing or finding out more about any of these offerings, please contact sales and a representative will be happy to help.
- Standalone security solutions are now part of multi-component bundles. This is a great benefit, as our bundles offer multiple component cover at no additional cost. Each bundle currently includes:
- ESET Endpoint Security for Windows/macOS/Android
- ESET Endpoint Antivirus for Windows/macOS/Linux
- ESET Server Security for Windows Server/Linux/Azure
- ESET MDM for iOS and iPadOS
How do I know if I need a cloud solution?
A deciding factor for cloud solutions is how ‘savvy’ your company is with managed or unmanaged software. Considerations such as whether you have in-house IT or employ ad-hoc IT support should also influence your decision.
ESET PROTECT Cloud (formerly ESET Cloud Administrator) is a cloud-based management console (offered as a service) which enables centralised management of select ESET products. ESET PROTECT Cloud enables you to manage your company's network security without the need to buy, install or maintain additional hardware.
Our sales team would be more than happy to discuss your company’s requirements and recommend the best ESET solution for your needs; contact them today.
I only need to protect my server, do I need to buy a bundle?
ESET Business bundles offer multiple ESET products under a single licence. This unique licencing system allows you to protect all of your company’s computers, laptops and smartphones using ESET solutions, without purchasing individual licences for each operating system
Can I try your solutions before buying?
Absolutely. If you want to see our ESET PROTECT management platform in action, try our interactive demo. No installation is needed and you can experience first-hand how your cloud management will look after few weeks of use.
If you are more interested in testing the full-feature licence, please request a free trial. You can install and deploy our protection solutions and test them free for 30 days, without any commitment. If you are interested, our experienced UK-based team will contact you and discuss any additional questions or specific business requirements you might have.
What are ESET’s advantages over other security vendors?
The cost of your digital security is not just the visible cost of a licence, but also the cost of managing it. ESET has a light footprint on your system, ensuring that there is little or no effect on your productivity or even your energy consumption; we call this The ESET Advantage. Find out how much ESET could save you annually.
What do users appreciate about ESET?
Verified customers appreciate that ESET has:
- Minimal system footprint
- Excellent malware accuracy
- Easy deployment and management
“Sleek interface and works as expected every time. All policies and remote administration is straightforward and thoroughly documented if there are questions.”
Read the full review and more on ESET’s G2 profile.
Pricing and Payment FAQs
Can I get a refund if I am not totally satisfied?
We are committed to our clients’ satisfaction and therefore offer a generous 30-day return policy. If you are not 100% satisfied with your purchase, we will be happy to provide a full refund of the purchase price.
How do I renew or add additional devices to my licence?
You can renew, enlarge or upgrade your licence at any time. This keeps your product up to date, maintains your uninterrupted protection, and ensures you have free access to our technical support as well as loyalty benefits.
- Start by logging into your account using your license key (XXXX-XXXX-XXXX-XXXX-XXXX) or public licence ID.
- To renew your licence, select the “Extend” option and adjust the period or number of devices you’d like to cover.
- If you want to add additional devices keeping the original expiration date, select “Enlarge” and adjust number of devices you’d like to cover. We’ll match the expiry date and calculate the pro-rated price for your extra devices.
If these options are not present in your account, it’s likely that your licence has already expired. If this is the case, we recommend purchasing a new licence.
What is automatic renewal?
ESET auto-renew ensures that your ESET licences and products are always up to date, providing continuous, year-round protection. We handle the billing and renewal for you using auto-renew, and you’ll be entitled to special renewal pricing.
By enabling auto-renew, you agree that at the end of your licence period, we will automatically renew your licence using the payment details currently on file. For more details, see our auto-renewal policy.
We will inform you about upcoming auto-renewal and renewal prices 30 days before your renewal date (for annual subscriptions) and after your subscription automatically renews, we will email you the transaction details.
How do I cancel my subscription?
Auto-renew is continuous, unless you turn it off after your purchase, via your account. Turning off auto-renew will not cancel your licence – your ESET protection will continue until your licence expires. We will notify you before licence expiration so you may renew manually.
You cancel automatic renewal at any time.
- Start by logging into your account using your licence key (XXXX-XXXX-XXXX-XXXX-XXXX) or public licence ID.
- Proceed to the Licence Management page, where you may use the “Auto-Renew” slider to cancel the renewal of your subscription.
- Confirm your selection to renew manually.
Related resources and documents
Discover more
Access our comprehensive PDF guide detailing all business solutions and their capabilities.
Use Cases
Phishing attacks and fake websites trying to steal login credentials are on the rise. See how ESET can help.
Technology
How ESET leading-edge technology goes far beyond the capabilities of basic antivirus?
Analysts and testing
Find out what industry analysts are saying about ESET, and how we perform in independent tests.
Explore other ESET PROTECT Platform tiers
Management Console Unified cybersecurity platform interface providing superior network visibility and control. Available as cloud or on-prem deployment.
Modern Endpoint Protection Advanced multilayered protection for computers and smartphones powered by unique ESET LiveSense technology.
Next-Generation
Antivirus Next-gen antivirus protection for business that helps you stay ahead of known and emerging threats with our AI-native, prevention-first approach.
Network Attack
Protection Fortifies your network infrastructure by blocking harmful network traffic directly on endpoints.
Device Control Enables restriction of unauthorised devices, such as USB flash drives or CDs, to prevent access to sensitive data, mitigating the risk of data breaches and insider threats.
Anti-Phishing Safeguards sensitive company data from phishing, spear phishing and other types of social engineering attacks.
Mobile Threat Defence Robust security for all Android and iOS mobile devices within the organisation. Equip your mobile fleet with Antimalware, Anti-Theft and MDM capabilities.
Full Disk Encryption Robust encryption solution for system disks, partitions or entire devices to achieve legal compliance.
Advanced Threat Defence Proactive cloud-based prevention against ransomware or never-before-seen threat types with autonomous remediation capabilities.
Vulnerability & Patch Management Actively track & fix vulnerabilities in operating systems and applications across all endpoints.
Mail Server Security An additional layer of security, protecting Exchange and IBM email servers from threats entering the network on top of the standard endpoint and file server protection.
Features advanced anti-phishing, anti-malware, and anti-spam combined with cloud-powered proactive threat defence. Provides you with robust quarantine management and rule definition/filtering system.
Prevents ransomware and other email-borne attacks without compromising email's speed.
Available as on demand upgrade providing additional protection layer. Click here and contact a sales person to receive an offering tailored to your individual needs. No commitment.
Available as on demand upgrade providing additional protection layer. Click here and contact a sales person to receive an offering tailored to your individual needs. No commitment.
Cloud App Protection Advanced protection for Microsoft 365 and Google Workspace apps, with additional proactive threat defence.
Available as on demand upgrade providing additional protection layer. Click here and contact a sales person to receive an offering tailored to your individual needs. No commitment.
Available as on demand upgrade providing additional protection layer. Click here and contact a sales person to receive an offering tailored to your individual needs. No commitment.
Extended Detection
and Response Additional platform capability to proactively detect threats, effectively identify anomalous behaviour in the network and realise timely remediation, preventing breaches and business disruption.
ESET Inspect, the XDR-enabling cloud-based tool, provides outstanding threat and system visibility, allowing risk managers and security professionals to perform fast and in-depth root cause analysis and immediately respond to incidents.
Unlock a higher protection tier with the added advantage of EDR included. Click here and reach out to our dedicated sales team to explore a tailored offering that meets your unique requirements. No commitment.
Starting at 25 devices.
MDR Service 24/7 managed detection and response service combining AI and human expertise to achieve unmatched threat detection and rapid incident response.
Available as on demand upgrade providing additional protection layer. Click here and contact a sales person to receive an offering tailored to your individual needs. No commitment.
Multi-Factor
Authentication Single-tap, mobile-based multi-factor authentication that protects organisations from weak passwords and unauthorised access.
Available as on demand upgrade providing additional protection layer. Click here and contact a sales person to receive an offering tailored to your individual needs. No commitment.
Available as on demand upgrade providing additional protection layer. Click here and contact a sales person to receive an offering tailored to your individual needs. No commitment.
Available as on demand upgrade providing additional protection layer. Click here and contact a sales person to receive an offering tailored to your individual needs. No commitment.
Premium Support
Essential Prioritised, accelerated and
guaranteed support from experts.
Available as on demand upgrade providing additional protection layer. Click here and contact a sales person to receive an offering tailored to your individual needs. No commitment.
Available as on demand upgrade providing additional protection layer. Click here and contact a sales person to receive an offering tailored to your individual needs. No commitment.
Available as on demand upgrade providing additional protection layer. Click here and contact a sales person to receive an offering tailored to your individual needs. No commitment.
Not sure what solution is best for your business?
Are you an existing customer?
Renew today
Renew, upgrade or add devices to your existing ESET subscription.
Manage licences
ESET Business Account is a licence management platform and entry point to ESET cloud services.
Installation
Install your purchased protection on additional devices.
Need assistance?
All ESET products include free technical support in your language.