
Our news about ransomware TeslaCrypt operators shutting up shop attracted a lot of attention and prompted several additional questions. So we’ve approached the best person to address them: Igor Kabina, the ESET malware researcher who first noticed that things had started to change around TeslaCrypt ransomware and ultimately created the universal ESET TeslaCrypt decryption tool.
TeslaCrypt ended happily with internet users getting rid of this ransomware, and its victims able to take advantage of a free decryptor. And, you played a crucial role in the latter, correct?
I asked TeslaCrypt’s operators to release the universal master decryption key for the latest, undecryptable version of TeslaCrypt. And they made it public. Having the key, I immediately started creating a decryption tool in order to make it possible and more convenient for ransomware victims to recover their files.
Put in a nutshell, it sounds simple. But it’s not that common to ask ransomware operators for decryption keys…
Yes, decryption keys are the ‘key’—literally!—to the whole ransomware business. It’s what the victims must pay for, if they fall victim to ransomware and don’t have a functional backup of their data. If you fall victim of this kind of cybercrime and you’re not prepared, you will find yourself in serious trouble.
But we quite often read about decryptors that enable victims to recover their files.
Yes, sometimes the bad guys employ weak encryption or make an implementation mistake that enables us to come up with a decryptor. But such solutions usually make use of a particular hole in the ransomware attack—and holes like these tend to get closed in the next version of the ransomware. That’s what makes this case different—thanks to the master key, I was able to implement a tool that can decrypt several of the latest TeslaCrypt versions at the same time.
OK, let’s get back to how you got the universal decryption key. We’ve learned that you simply requested it from the malware’s operators. Was it really that simple?
For quite a long time, I’d been keeping an eye on TeslaCrypt ransomware—it’s my job to keep pace with developments in malware, in order to help keep ESET clients safe. I witnessed earlier versions of this ransomware which, thanks to bugs inside them, allowed a decryptor to be created. Unfortunately, the latest versions of TeslaCrypt came with an improved key protection algorithm and so were really powerful.
Knowing how a typical malware lifecycle looks, I expected further development of TeslaCrypt. But several weeks ago, I noticed that development had started to slow. It seemed to me that the operators were about to quit—incidentally, some of the groups who distributed TeslaCrypt had started to switch to another brand of ransomware, CryptProjectXXX.
On April 27, a version that later turned out to be the very last version of TeslaCrypt was compiled. Soon after that, I noticed that the people behind it had stop spreading this version and that all the links they used were slowly dying. So I tried my luck, pretended to be one of their victims and asked them if they would be so kind as to release all four of the private keys they had been using since TeslaCrypt started. They answered me in one day, which was their usual response time, but provided me only with the key for the victim I was pretending to be. I asked them again if they could, as a gesture, release at least the latest (4th) universal private key. A day and a half later I noticed that a “project closed” announcement had been posted on the TeslaCrypt page. At first I didn’t believe they had really released the key, but after I checked the corresponding public key I was 100% sure it was the right one.
One question comes to mind as you speak about your contacts with these malware operators. Is it common for malware researchers to talk to the guys on the dirty side of the business?
Let me be clear that all the communications ran via the official channel that the bad guys had created for communicating with their victims. Think of it as normal software help desk. Since it’s anonymous, the operators had no idea who they were communicating with—I was pretending to be a random victim of TeslaCrypt.
And now let me answer your question: no, it’s not common for malware researchers get in touch with the bad guys, but in this case it seemed to be worth a shot.
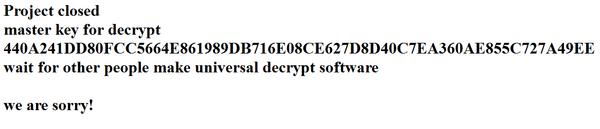
The closing announcement reads “We are sorry," but they caused so much harm to their victims…
As with CryptoWall, they claim they are helping people and are testing antivirus solutions. I strongly disagree: they only want to steal money. On the other hand, the operators or creators of TeslaCrypt have shown that they have at least a modicum of good faith, because they have provided decryption keys in several cases for free in the past. However, that doesn’t make up for all their malicious acts.
What’s the moral of this story? What can internet users learn from it?
People should learn more about how to use computers and how to protect themselves against threats. They should continue to be cautious when opening attachments and links. Of course, keeping your system and applications updated and patched is a must, along with having a reliable and properly-configured security solution running. And having a functional offline backup is crucial.
Antivirus companies are doing what they can, but unfortunately there is always a human factor, which is what the bad guys target, using social engineering. People should realize that when they are hit by ransomware, it is not about their files. The creators of ransomware do not care about files: they care only about money. I know it is hard to lose important files, but we always recommend not that you do not pay the ransom. When people stop paying ransoms there will be no ransomware in the future. In the meantime, people should know that there are good guys out there who are doing their best to protect them, and who take every opportunity to help.
To better understand ransomware and how to protect your files and data, download this free guide to ransomware security.
This article originally appeared on ESET’s blog WeLiveSecurity.com.