Earlier this year, Whalebone, a provider of Whalebone Domain Name System protection services, tested the quality of Indicators of Compromise (IoC) on dangerous domains provided by ESET.
Testing has shown that by including the IoC from ESET Threat Intelligence, detections significantly increased, with false positives amounting to virtually zero. Overall, the test has proved that it is appropriate to use ESET Threat Intelligence as a source of IoCs for DNS-level protection.
ESET Threat Intelligence provides global knowledge on targeted attacks, advanced persistent threats (APTs), zero-days and botnet activities. It closes the gap between the cybersecurity information that security engineers get from their own networks and the vast amount of cyberspace intelligence that ESET collects worldwide, using information gathered from more than 100 million sensors. This allows customers to turn unknown threats into known and mitigated threats, thereby improving the effectiveness of their defenses.
The tests were carried out in the first quarter of 2018 on a sample of nearly 100,000 Internet connections in the Czech Republic and Slovakia, which represents approximately half a million connected devices. The objective of the test was to verify the quality of the feed provided by ESET Threat Intelligence. Within the test, Whalebone scrutinized the number of domains blocked and the number of false alarms, comparing ESET’s feed performance with Whalebone’s other sources of IoC. (Before the test, there was no endpoint protection vendor included amongst Whalebone's data suppliers.)
ESET, as a provider of IT security solutions and services, and because of its size as well as technological maturity, generates a significant amount of valuable data. We regularly leverage this data to protect our customers - and also offer it to our partners and clients in the form of ESET Threat Intelligence services.
Whalebone, one of ESET's partners, has added a data feed from ESET – the raw intelligence feed – to its existing DNS/domain blocking resources. ESET's systems process hundreds of millions of URLs and tens of millions of domains per day. Out of those, tens of millions of URLs and millions of domains are unique. ESET utilizes this data in its URL blocking technology which is one of the layers of protection of ESET’s security solutions and plays an important role in that it can block malware that could potentially pass through other layers of protection. The URL blocking technology provides effective protection, but has some specifics that need to be taken into account. Otherwise, there is a risk of complications, especially in the form of false alarms.
First of all, URLs can be blocked for a number of reasons. Secondly, there can be different classes of URLs on a single domain, including clean URLs. This leads to the need for detailed classification.
ESET uses more than two dozen states of URLs and domains for classification. In contrast to ESET’s URL blocking technology, Whalebone’s technology is domain-based. For this reason, URL states are useless for Whalebone.
Detailed classification allows ESET customers to set up internet protection according to their specific needs. The four basic conditions to which the classification of domains may be narrowed down to are:
1. BLOCK (malicious domain)
2. PHISHING (phishing domain)
3. UNWANTED (domain with potentially harmful content, typically scams)
4. BLOCKED_OBJECT (domain with malicious executable(s))
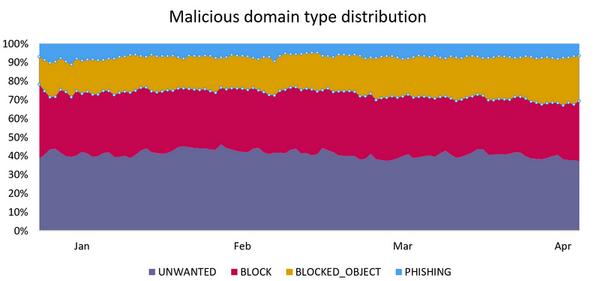
The four mentioned basic domain states were reduced to two fundamental ones, BLOCK and PHISHING for the purposes of Whalebone’s domain blocking. The other two states are known to be prone to generating false positives, a phenomenon that only multi-layered security solutions can tackle successfully:
- BLOCKED_OBJECT: The domain usually contains a lot of clean pages and only a small number of malicious files on specific URLs.
- UNWANTED: The domain usually contains fraudulent offers or coin miner scripts; however, some users may want to access such content.
Due to time sensitivity, it's very important that the data arrive at Whalebone as soon as possible. Thus, the feed is generated every 5 minutes on ESET's side, and then uploaded in the STIX format - a standard security information format - to the TAXII server. From it, Whalebone downloads the data and imports it into their system.
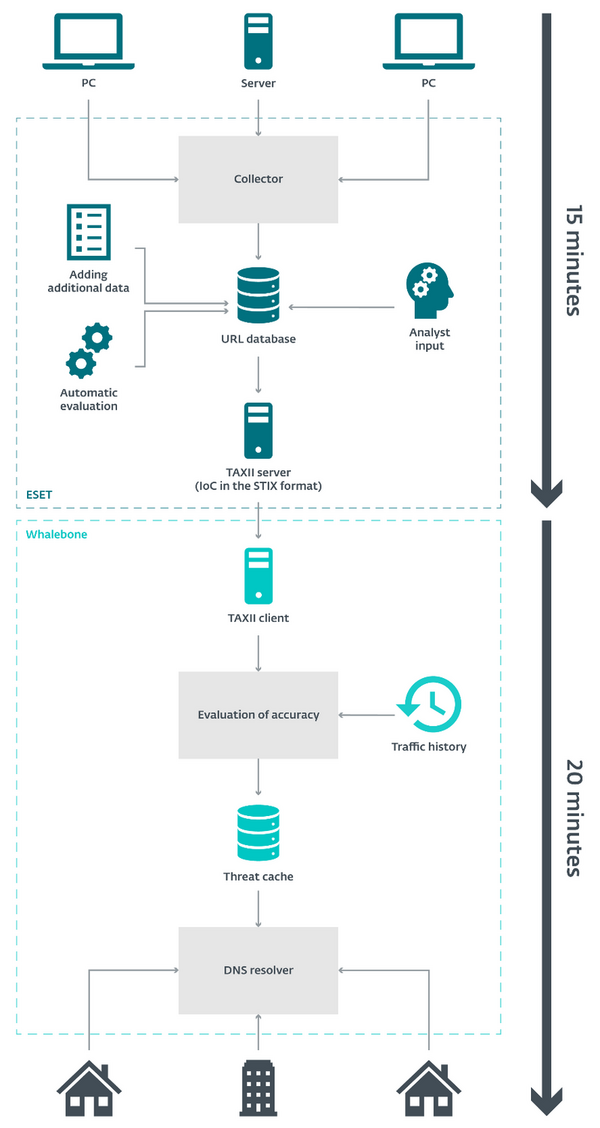
Whalebone processes the downloaded data at several-minute intervals and applies it in the Whalebone detection engine. If any of the malicious domains don’t get detected for more than three consecutive days, the domain will be removed from the list of active threats.
Results of the Whalebone test
During the test period, spanning from the beginning of 2018 to half-April 2018, around 55 thousand unique malicious domains supplied by ESET were processed in the tested IoC feed. Out of those, around 1100 domains were detected in the traffic from connected devices in the Czech Republic and Slovakia.
18.5% of the devices in the test made at least one attempt to contact a malicious domain from the whole feed (i.e., IoCs supplied by ESET and all other sources). The overall number of incidents in the test was around 1.75 million. Out of those, around a half (866 thousand incidents, precisely 49.51%) were detected based solely on IoCs provided by ESET – i.e., without data from ESET, these incidents would have gone undetected. Only 0.47% of incidents were detected based on both ESET’s and original Whalebone data; the remaining 50.02% of incidents were detected independently from ESET.
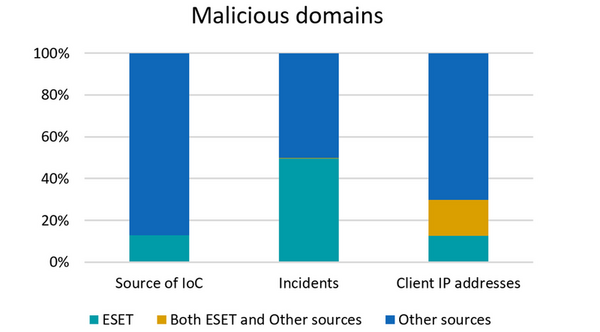
Out of all the incidents detected based on IoCs by ESET, only one single domain blocking was found to be a false positive.
Testing has shown that by including the IoCs from ESET Threat Intelligence, detections significantly increased, with false positives amounting to virtually zero.
Overall, the test has proved that it is appropriate to use this source of IoCs for DNS-level protection.
Note: this article is based on the joint Whalebone-ESET presentation “Testing threat intelligence data for DNS protection” by Robert Šefr, Whalebone; Jakub Daubner, ESET; Peter Dekýš, ESET. The presentation was held in May 2018 at the IS2 Conference, Prague, Czech Republic. Unfortunately, the conference proceedings are only available in Czech.