If the recent 2019 ESET Global Press Event was any indication, with its 57 international journalists and nine presentations, cybersecurity has become Tier 1 news. The event was flavored with a healthy dose of IoT threats, APT activities, cyberespionage and more common threats like sextortion and mobile malware. The takeaway for many was that this diverse and complex threatscape could use a guidebook.
Actually, that guidebook already exists. The MITRE ATT&CK™ knowledgebase has developed into a popular common taxonomy among IT security professionals, including incident responders, network defenders, threat intel analysts and malware researchers—all of whom have contributed to help enterprise management gain a better assessment of the digital threats to their businesses.
While ATT&CK’s knowledgebase widens and deepens, endpoint security vendors and their clients still have some critical business to attend to: communicating and taking both proactive and reactive steps to leverage the information already assembled by malware researchers. At ESET, and at other vendors, this engagement takes place via an endpoint detection and response (EDR) tool – ESET Enterprise Inspector.
ESET Enterprise Inspector
The solution includes about 300 predefined configurable rules to detect potential threats in multiple execution configurations and enables:
- Behavioral detection to identify, categorize and alert
- Threat hunting + blocking of suspicious executables and processes
- Network visibility via open architecture
- Context-aware investigation & remediation
- Incident detection (root cause analysis)
- Data collection on newly executed modules, including: time of execution, user, dwell time and attacked devices
- (IOC) detection
- Anomaly detection
- Company policy violations
Many of the early rules had their primary origin in our Host-based Intrusion and Prevention System (HIPS). These were expanded by collating and auditing external open-source data, an effort that ultimately led the ESET team to ATT&CK. The knowledgebase provided valuable hints to help order, best document/classify and match tactics to detection rulesets included in ESET’s EDR tool.
EEI is interactive and iterative
Like the “widening and deepening” ATT&CK knowledge base, EEI is evolving as it leverages ESET's global network of over 110 million endpoints to rapidly detect and remediate emerging threats. Throughout its buildout ESET engineers and researchers have generated new ideas, received requests and both encountered attack vectors and tactics that needed to be reflected in both ruleset creation and the platform’s functionality.
In version 1.3, released in September 2019, ESET specifically leverages ATT&CK’s taxonomy/tactics to build part of its ruleset. This is, of course, heavily bolstered by ESET’s own research and documentation of malware and APTs. The native rulesets in EEI are in fact written by ESET’s Malware Research team and delivered with 313 rules by default.
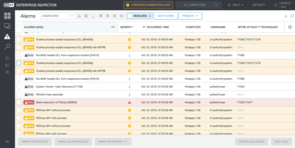
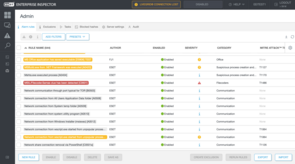
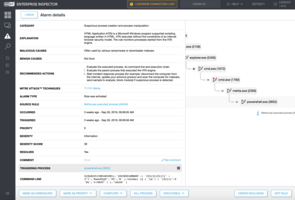
(Image 1. above) Default rulesets automatically trigger alarms in EEI. Additionally, EEI users can reference the ATT&CK knowledgebase directly from the dashboard.
While this is a clear improvement to the GUI, the true benefit runs deeper. That benefit stems from the engagement/interactivity taking place between the client-side user(s) of EEI and the EEI system itself, and the critical dialogue that can occur between users and ESET’s malware analysts/engineers.
Specifically, security engineers at an enterprise’s SOC need to understand better how to draw out more value from threat intelligence sources and leverage that intel to cut through the avalanche of false alerts that often plague network defenders’ EDR dashboards. That is where the rulesets, details on malicious and benign causes, and recommended actions built into EEI and coupled with references to MITRE ATT&CK techniques come into daily play.
To learn more about how ESET employs ATT&CK for improved endpoint protection, join our November 13 webinar.
Learn more about ESET Enterprise Inspector’s Strong Performer status in the Forrester Wave™: Endpoint Detection and Response Q3 2018 report.
