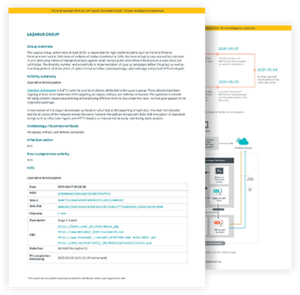
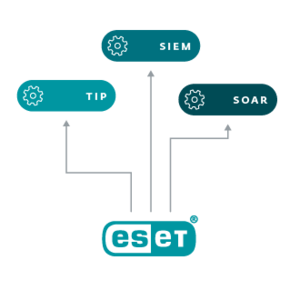
Threat Intelligence reports and feeds
Get unique intel, stronger defenses
Threat intelligence from ESET's world-renowned experts. Get a unique perspective on the threat landscape and improve your cybersecurity posture.
Threat Intelligence reports and feeds
Get unique intel, stronger defenses
Threat intelligence from ESET's world-renowned experts. Get a unique perspective on the threat landscape and improve your financial institution's cybersecurity posture.
Get unique insights
ESET gathers threat intelligence from a unique range of sources and has unparalleled in-the-field experience that helps you fight increasingly sophisticated cybersecurity attacks.
Get unique insights for financial institutions
ESET gathers threat intelligence from a unique range of sources and has unparalleled in-the-field experience that helps the financial sector fight increasingly sophisticated cybersecurity attacks.
Stay ahead of adversaries
ESET follows the money, specifically monitoring those places where we have detected APT groups that target Western companies: Russia, China, North Korea, Iran. You’ll know about new threats first.
Make crucial decisions, faster
Anticipate threats and make faster, better decisions thanks to comprehensive ESET reports and curated feeds. Reduce your exposure to prevailing threats, forewarned by experts.
Improve your security posture
Informed by ESET intelligence feeds, enhance your threat hunting and remediation capabilities, block APTs and ransomware, and improve your cybersecurity architecture.
Automate threat investigation
ESET technology searches for threats constantly, across multiple layers, from pre-boot to resting state. Benefit from telemetry on all countries where ESET detects emerging threats.
Access unparalleled expertise
ESET has invested in building the world’s leading cybersecurity team, and 13 R&D centers worldwide. We use machine learning to help automate decisions, but our people stand behind threat evaluation.