A case for cloud sandboxing and endpoint detection and response
Surveys and white papers consistently show that organizations identify ransomware breaches/attacks among their biggest security concerns. These often outweigh far more advanced threats like targeted attacks or cyberespionage that can go unnoticed for years, in which attackers sift through targeted networks for valuable documents, data and credentials.
Simply put, a ransomware attack on an unprotected and unprepared organization may put it out of business. Threatening business continuity and reputational damage, the specter of ransomware is forbidding, though ransomware is just one of many payloads that can be dropped into a network. However, ransomware may be considered a litmus test for the security state of the network in question.
Pass or fail, countering ransomware, via preparation and/or dealing with an existing attack, sets an organization on a journey to evaluate, organize and prepare for a more engaged and ultimately critical mission: building a dynamic defense based on properly managed endpoint security technology and a well-educated security team.
Capacity is king and…
To defend systems at an enterprise level, IT security teams must A. pursue ongoing education to broaden and deepen technical capacities and B. take advantage of new solutions that provide additional layers of security that go beyond the standard detection technologies provided by an endpoint security suite. The fact is, this is not an either-or; a balanced approach is the ideal, and it is critical.
Achieving that “ideal” is an ongoing quest, one often made more difficult by persistent shortages of cybersecurity talent. As such, addressing capacity constraints via technical solutions immediately comes into play. Deploying a comprehensive endpoint protection platform, especially one that adds mail protection and cloud sandboxing analysis, can go a long way toward protecting an enterprise. That said, with threats like ransomware being deployed as payloads of more complex malware, many security teams stand to face a big step up in both defending against and understanding their adversaries.
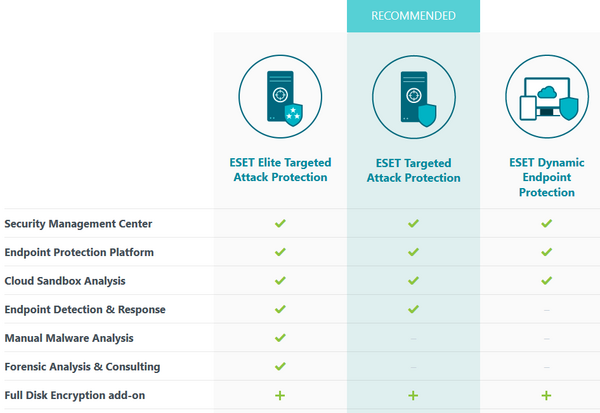
(Image above: In the portfolio hierarchy of endpoint protection bundles, ESET Dynamic Endpoint Protection is followed by ESET Targeted Attack Protection.)
To that end, ESET offers both bundled solutions and standalone upgrades. Our recommended bundle, ESET Targeted Attack Protection, goes beyond just management and protection, adding ESET’s powerful Endpoint Detection and Response (EDR) tool, ESET Enterprise Inspector (EEI). In this way, the level of security is increased via a better understanding of the unique threats facing a corporate network and its defenses.
Tech adds teeth
While EEI boosts understanding, for teams facing capacity bottlenecks or who need intel in real time, adding ESET Dynamic Threat Defense (EDTD), which employs machine learning models in a cloud sandboxed environment, allows for significant automation of the analysis of threats (including Zero Days).
With EDTD’s main function being to analyze potential threats, for example those often hidden in email attachments, it has been engineered to be able to (among other things) simulate user behavior in order to trick the anti-evasive techniques of some malware. The resulting analysis of that particular behavior is that attachments that are classified as malicious are stripped from the email, with the recipient receiving a notification* about the detection. Simultaneously the application builds out a behavioral report of the detected malware for the IT administrators, which is accessible in the ESET Secure Management Center (ESMC).
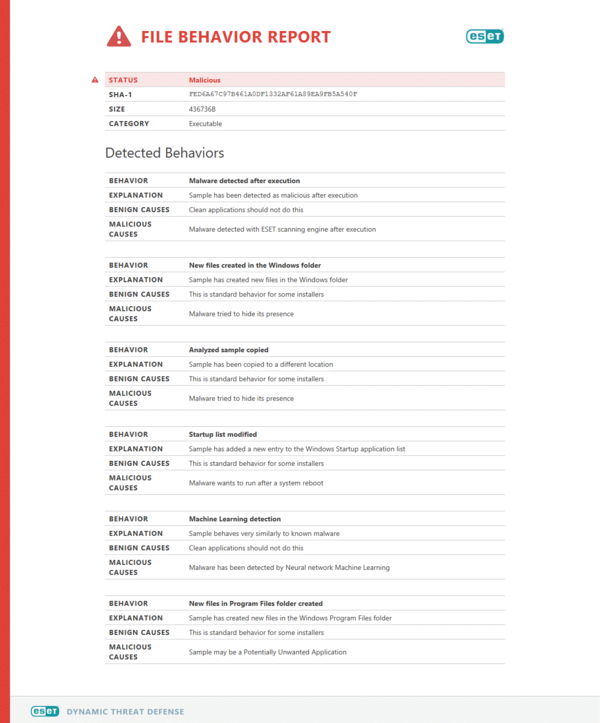
*(Image above: EDTD File Behavior Report – IT security team selects a suspicious file and receives a report that includes the user and machine that was the source of the sample.)
When coupled with ESET Mail Security, EDTD acts as a network layer defense (Download PDF) by preventing endpoints from encountering any detected malicious emails. Under the hood, EDTD’s sandbox consists of a number of mechanisms that complete static analysis of code via deep inspection of the sample with machine learning, in-memory introspection and behavior-based analysis.
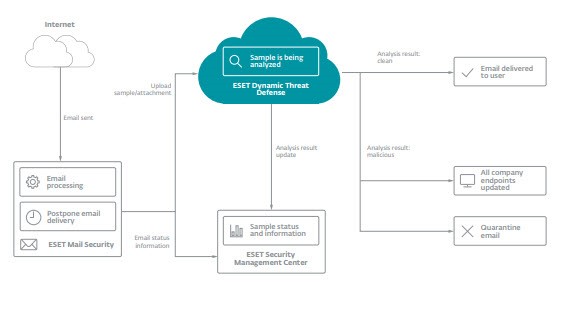
(Image above: journey of an email processed by ESET Mail Security and its subsequent trip to EDTD.)
Human led, machine supported
Regardless of your security team’s level of IT security or experience, the number and complexity of digital threats crossing paths with your team and the suite they manage make it easy to forget that the true adversaries are all too human. EDTD empowers your team to maintain daily protection while allowing them more time to gain perspective and to learn more about specific threats facing your organization. In any case, these tools help ensure teams have the capacity needed to safely evaluate and mitigate ransomware and other advanced persistent threats that try to gain a foothold in corporate networks via malicious emails, documents and other files.
So, to protect against ransomware and analyze new threats to IT infrastructure, consider the additional layers of security provided by cloud-based sandbox technologies like ESET Dynamic Threat Defense (EDTD), and remember that ransomware is a litmus test. It’s just a starting point of a longer journey. Improve your odds with EDTD.
____________________________________________________________________
For further information on how to protect your company against ransomware and similar attacks, please see these useful resources:
- RANSOMWARE: an enterprise perspective
- Ransomware FAQ
- Best practices to protect against Filecoder (ransomware) malware
- ESET vs. Crypto-Ransomware
Interested in putting more power into the hands of your IT security team or SOC?
Check out ESET Enterprise Inspector.
