Discover the game-changing insights from ESET World 2025, where IDC's Craig Robinson and Chris Kissel reveal why MDR is invaluable, and how threat intelligence is the secret weapon for company security.
What makes the managed detection and response (MDR) market as valuable as it is, and how essential is threat intelligence to maximizing company security?
For answers, look no further than the ESET World 2025 presentations by IDC’s Craig Robinson, research vice president, security services, and Chris Kissel, research vice president, security and trust product. The former offered insight into the state of the MDR market, while the latter discussed the intricacies of threat intelligence. Let’s dive in, shall we?
The state of the MDR market
Robinson held the first session, taking the stage with a lot of enthusiasm. He opened his presentation with the premise that company size doesn’t matter, as even the most financially productive corporation can have around 22% of its cybersecurity tools improperly configured or managed. “That’s like taking euros out of your wallet and burning them. … If you’re paying for stuff that doesn’t work, that’s just crazy.”
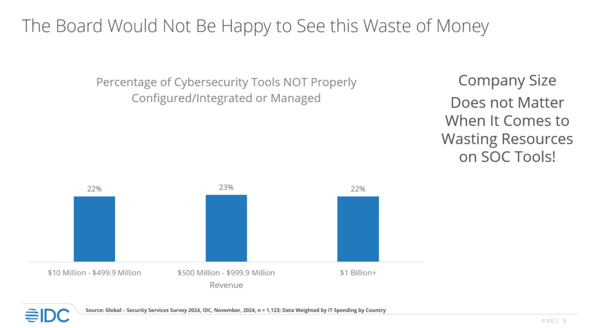
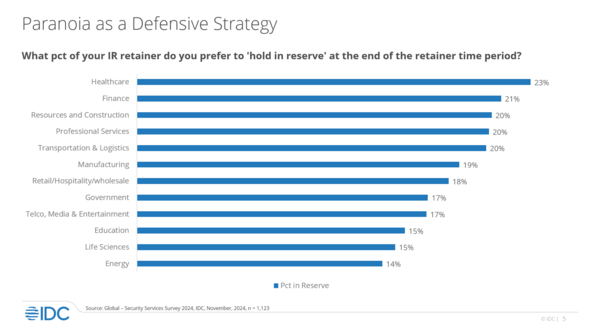
He continued by describing the “paranoia strategy,” saying how businesses reserve certain amounts of money for “bad days,” such as the end of the year, as threat actors tend to attack when businesses are the least ready. But is it wise to do that?
The MDR journey
Robinson followed by making a case for MDR: “When you look at the number of tools … platforms, the things we utilize to try and keep us safe, it’s a whole bunch of stuff, and it’s hard for us to do sometimes.”
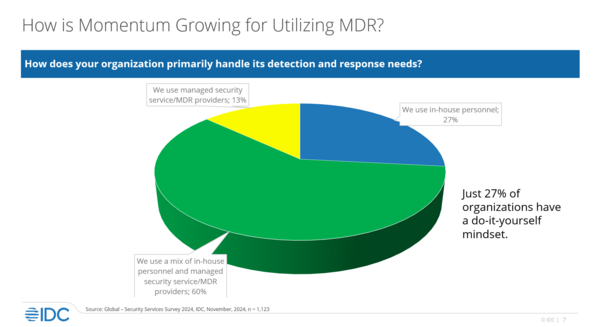
The key is to decide whether a company is capable enough to handle detection and response on its own — based on IDC’s findings, only 27% do so. “The rest of us recognize [that] it’s OK to get help. And one of the ways you can do that is by utilizing capabilities like managed detection and response,” Robinson said.
What are the building blocks for an effective MDR program?
Robinson then went on to describe what makes an MDR program really work. He did so through an analogy, referring to the building blocks of MDR:
- Monitoring: “You need humans, [and] that’s one of the key things MDR does.” As one needs a minimum of 13 people to manage a Security Operations Center, MDR offers constant monitoring beyond what in-house SOCs can offer 24/7.
- Detection: By professionally using EDR/XDR/SIEM, MDR providers can sift through all the noisy alerts to detect and stop real attacks, while not wasting time on false positives. In combination with threat intelligence feeds, it’s powerful.
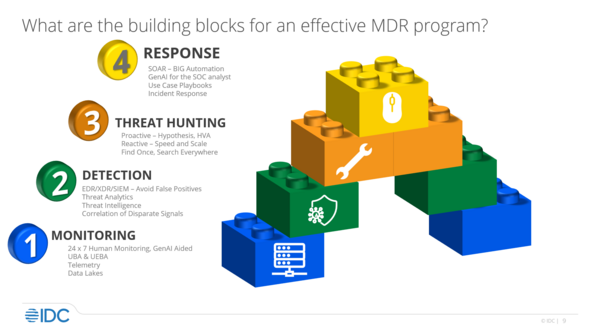
- Threat hunting: “When you utilize an MDR provider, if they see something in one of their customers, they have a responsibility to check the rest of their customers. ... That’s how the synergies of having a large pool to look at benefits us.” By combining proactive and reactive hunting, MDR can check low-level alerts and triage the most important ones at the same time, covering an entire attack surface.
- Response: Here, automation is essential. Tools like SOAR, or GenAI for SOC analysts, can immensely speed up threat response. “GenAI helps to guide us in a much quicker and, hopefully, analytical and smart way,” Robinson said.
An effective solution needs human experts at its core. The systems they must handle include more complex solutions, such as cloud detection and response or threat intelligence. Beyond these, there are additional technologies like SIEM or machine learning that empower faster detection and quicker response.
Positive outcomes are thus measured by success in achieving quicker times to detect and respond, as well as by lowering the assumed costs an incident could generate: “MDR is such a no-brainer when it comes to saving money. When you add up all the costs, and try and put all this stuff together on your own… what’s the budget gonna look like? Scary … especially in the SMB space, it [MDR] makes a ton of sense,” Robinson suggested.
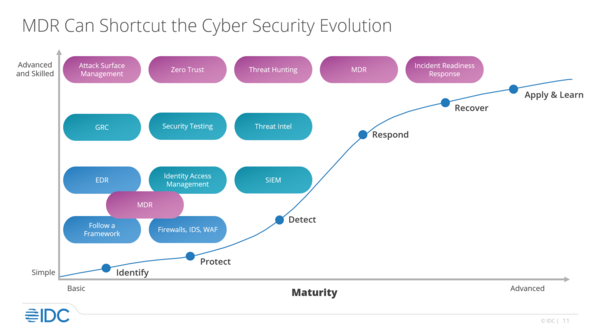
MDR as a security shortcut
Robinson provided an excellent overview on how MDR can help an organization leapfrog security maturation: “All you really need is EDR and an MDR provider. You don’t need to spend money on all the other stuff. … It’s good, but if you’re not evolving … then you’re gonna fall behind and not be a viable organization any longer,” Robinson described.
The contribution of GenAI
IDC has surveyed some companies regarding themes connected to GenAI, with most looking for enhanced efficiencies it could bring. However, around 5% of those surveyed said their MDR doesn’t employ GenAI, which Robinson sees as a red flag:” When they’re not doing it, dump them, because they’re not evolving. So if they’re missing GenAI, what other things are they missing?” he asked.
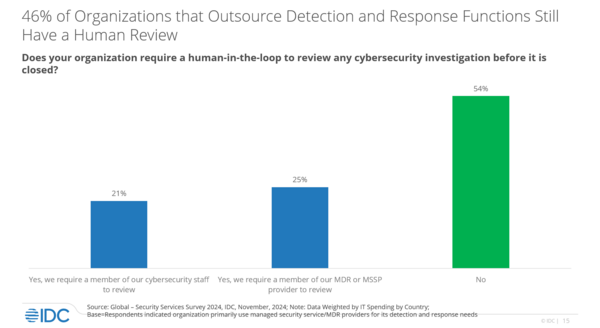
Likewise, around 54% of respondents don’t even review their cybersecurity investigations before they’re closed. Robinson argued that human review is essential (especially when dealing with AI detections), but not for every case, which MDR can easily supply.
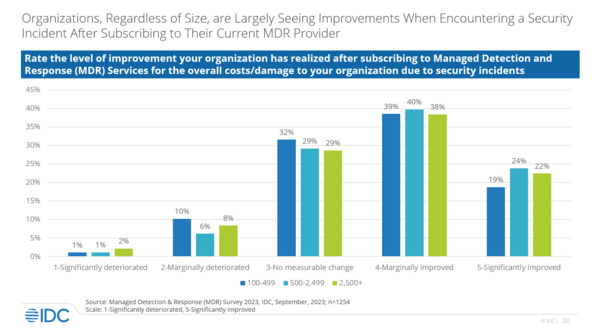
All in all, organizations, regardless of size, are largely seeing improvements after subscribing to MDR. “Why? Because you’re working with a team of people whose core competency is detection and response,” elaborated Robinson. Incidents are an eventuality, but with MDR, the costs can be as small as possible.
Factors to consider with MDR
Thus, the top factor when considering MDR is cost-effectiveness: “It all comes down to efficacy. Does it work? ... Is it the best use of my dollars?” said Robinson.
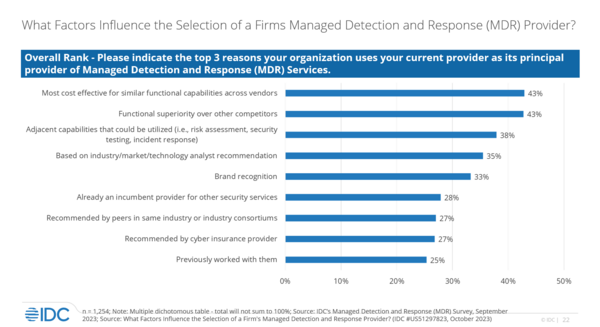
The right MDR provider supplies both guidance and a human element: “You want to be able to talk to someone. Do they talk to me, or am I just a number?” said Robinson. This human element is also present in ensuring the required tenure and experience, as the more professionals a vendor retains in the long term, the better its consistency in spotting threats. In addition, growing businesses might find security upgrades painful, but MDR can ease that.
For larger organizations, co-managed options are relevant to building an understanding of their security needs. Lastly, MDR lowers cybersecurity premiums. If an organization is unsure about providers, the insurer might also have recommendations.
Threat intelligence: How high the fence should be
Robinson then handed the stage over to Chris Kissel, who elaborated more on the essential benefits of threat intelligence (TI).
Businesses can’t control only their perimeters. They have to worry about their data, network, identities and apps, and endpoints. However, businesses don’t know what happens beyond these areas. Moreover, misconfigurations and endpoints falling out of management make even said perimeter difficult to maintain. “No matter how hard you try to make your security surface pristine, it’s almost impossible to get there,” said Kissel.
Plus, adversaries are as varied as their attacks and tactics, techniques and procedures (TTPS). It’s a confusing world, but with threat intelligence, perhaps the perimeter walls can be adjusted accordingly.
Important aspects of threat intelligence
Kissel then went on to describe aspects of TI that are critical, saying that TI can be utilized dynamically, without creating a digital debt (meaning having to use compute power).
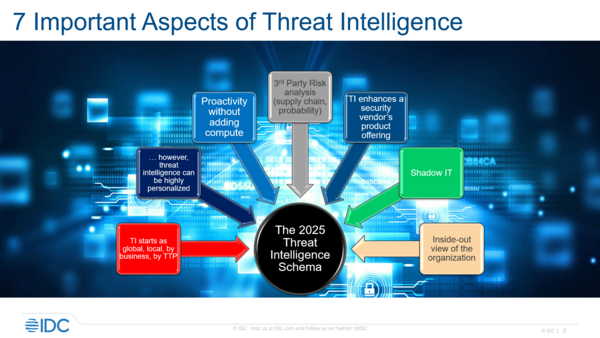
TI essentially enhances what businesses already have in store — continuously adding data to inform existing solutions and personnel, easing security decision-making processes.

It’s imperative that TI data is low on false positives and incorporates data from simulations, tying into threat hunting efforts as well. Companies that use multiple feeds, with data also coming from research labs, offer TI that can provide novel insight into business networks.
“Threat intelligence should tell you unique things that you don’t yet know about your network … essentially, various blind spots for an organization seen from the outside in, and then it also takes everything that happens on the internet and tries to apply that context to your world,” Kissel said.
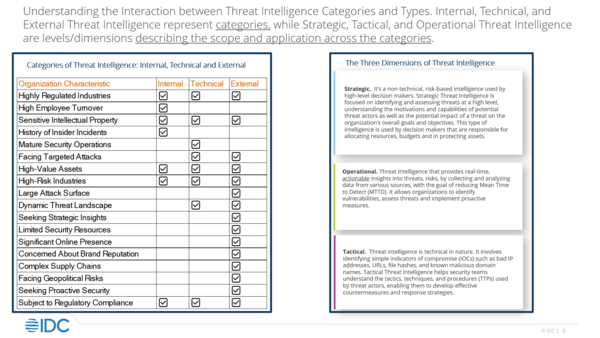
With TI’s multiple dimensions, businesses need to consider the best way to apply TI to their security playbooks. This should be based on company characteristics, such as available security resources or assets.
TI forecast
IDC expects threat intelligence revenues to grow 19% year over year through 2029. However, Kissel’s suspicion is that there’s going to be a shake-up in the intelligence area, with less data sharing between intercontinental partners. With that said, multinational organizations can make up for that by subscribing to several different threat services feeds.