Threat Intelligence is experiencing a renaissance – as a now invaluable tool for threat hunting experts, its power can be doubled by offering the right feeds and some AI help.
Intelligence operations aren’t the sole property of state agencies. Cyberthreat intelligence, as compiled and curated by cybersecurity vendors and researchers, is what delineates the difference between a professional SOC and a general security operation.
Threat Intelligence in and of itself, is not a free ticket to security stardom though. No, it requires a specific approach that can harness the knowledge contained within. Is the investment worth it though, and if so, how to make the most of it?
The state of threat intelligence
Analysts predict that threat intelligence will play a key role in the years to come, as more companies invest into building up their own capabilities. Researchers expect the current market to double by 2028.
The reasons driving demand are simple – cyberattacks are becoming more complex. What used to be a case of viruses infecting PCs through removable media, is now characterized by sophisticated ransomware such as Embargo, which tailors its tools to each victim specifically. In this case, Embargo uses MS4Killer, an endpoint detection and response (EDR) killer, which abuses Safe Mode and a vulnerable driver to disable selected security solutions.
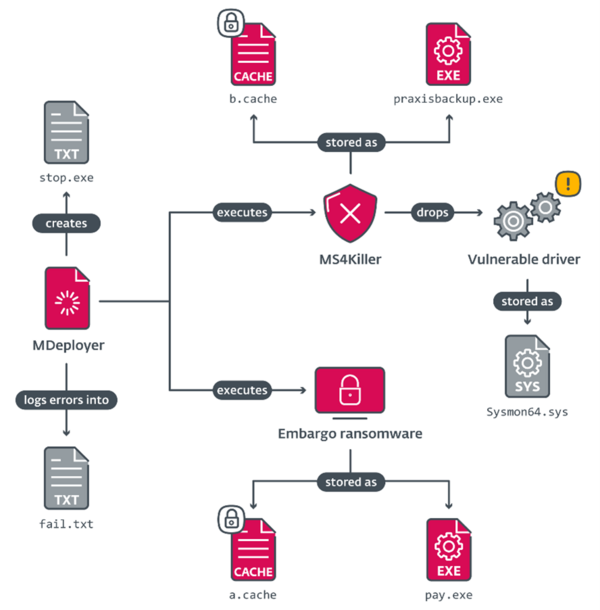
Malware execution diagram of Embargo ransomware. (Source: ESET Research)
However, with the right threat intelligence solution operationalizing a response wouldn’t take long. For example, with ESET Threat Intelligence (ETI), a security analyst could more easily analyze detections, locating additionally relevant data points, better informing their decision on what sort of adversary they are dealing with. Hence, the decisions to be made during a response would come from a more informed place, preventing mistakes in siloing/blocking off the wrong processes/systems with their EDR/XDR tool of choice.
That’s why the state of threat intelligence has such a bright outlook, as among the cornucopia of security tools, it is one of those that can effectively augment existing processes.
Finding the right feed
One of the key aspects of threat intelligence are data feeds. Imagine them as curated flows of real-time data, much akin to having a customized RSS or news feed. They deliver exactly what an analyst needs, so when they’d like to know more about threat emanating from malicious files, they could subscribe to one such feed and learn more about newly discovered malware samples, or indicators of compromise (IOCs).
Having multiple feeds at once, or just subscribing to specific types can greatly enhance an organization’s ability to respond to threats. As of 2025, ESET Threat Intelligence now provides 15 different feeds and 2 sub-feeds, such as ones specifically focusing on Android threats, IoCs, Botnets, phishing URLs and more.
These feeds, each tailored to a different security topic, help analysts become more proactive. Seeing how a particular type of malware works, its type, hashes and other information informs the creation of better and more timely security decisions. An Admin might say: “If I know that this technique is related to Embargo ransomware, then I’ll recognize which particular processes to target, like suspicious registry modifications.”
In fact, ESET Threat Intelligence now also provides a separate Ransomware feed, which together with our offer of APT Reports can enable businesses to stay ahead of sophisticated threats such as Embargo.
Remember, an APT won’t wait on its victim’s remediation efforts, they’ll brute force and escalate their attempts for success, but having the latest knowledge on their tactics, techniques, and procedures (TTPs) might just be the missing ingredient a SOC needs.
The more the merrier?
So, where to find these feeds? Luckily enough, many security vendors (especially those with research labs) offer solutions that provide them, along with many other functions. Some go as far as to create integrated solutions that pull in data from a vast array of intelligence providers. Most often, a security operation uses as many as 9 different TI source vendors at once, enriching their view of the worldwide threat landscape.
The reason for this is that when an Admin browses the MITRE ATT&CK database or VirusTotal, they can see how vendor detections differ, then combining them into a broader picture. As each vendor tackles telemetry differently, the surefire way to create proper attribution is through comparison, as evidenced here by a particular ESET MDR story on Mallox ransomware.
Does it make sense to subscribe to every feed there is? Not really. There’s something to be said for having just the right amount of actionable, high-quality information. For all else, that’s where AI enters the picture.
Reducing the complexity of threat intelligence
Automation is all the rage these days, and for a good reason. Besides the notion of “AI” being stuck on top of everything (even where it doesn’t make sense), the road that paved the way was and still is, machine learning.
With machine learning, the possibilities are numerous. Inside a security solution, it enables behavioral detection, DNA code analysis, or threat mapping, all of which helps bring down detection times and the rate of false positives. This is a result of continuous learning, which uses algorithms to study ingested data to make predictions based on various patterns.
So, placing a generative tool like the ESET AI Advisor inside ESET Threat Intelligence, it can use data from our APT Reports to the benefit of an analyst. Simply by asking it to detail relevant APT activities to a company’s profile, it could highlight the right threats to watch out for.
Putting our best research at your fingertips
Written in concise, actionable language to improve organizational security, ESET APT Reports provide detailed insights into malware campaigns, distribution, and actors involved. This supplies a great deal of strategic advantage, helping make crucial decisions faster. With APT Reports Ultimate, customers also have access to an ESET analyst for up to four hours each month, providing an opportunity to resolve any outstanding issues.
This optimizes analyst workflows and individualizes the solution in use. No more discussions about the right feeds to use, or time spent perusing reports and research pieces. Just ask a question, that’s all there is to it. Alternatively, integrate ESET Threat Intelligence with your management platform of choice, and have your systems make those decisions for you.
Unlock your confidence
Knowledge is power, and what is power’s source if not the confidence to make the right decisions? While this is more of a philosophical question and warrants some scrutiny, it perfectly describes the value in threat intelligence. For if a SOC wants to actualize their potential, they have to make confident decisions during incident response, a proposition that is only possible if properly informed.