Modern Endpoint Protection
An endpoint protection platform (EPP) is a security solution deployed on company devices to prevent cyber attacks, detect malicious activity, and provide instant remediation capabilities.
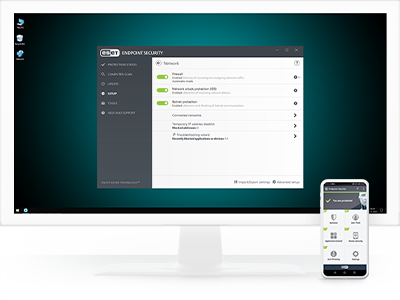
ESET Endpoint Security
Powerful multilayered protection that leverages ESET's unique global threat detection network, machine learning capabilities and human expertise.